Anti-forgery token is used to prevent CSRF (Cross-Site Request Forgery) attacks. Portal will manage authentication and authorization, so no authentication code is required. However, you need to include CSRF token with all web API requests.
Cross-site request forgery is an attack against web-hosted apps whereby a malicious web app can influence the interaction between a client browser and a web app that trusts that browser. These attacks are possible because web browsers send some types of authentication tokens automatically with every request to a website. This form of exploit is also known as a one-click attack or session riding because the attack takes advantage of the user’s previously authenticated session. Cross-site request forgery is also known as XSRF or CSRF.
The following are some of the anti-forgery token related error messages you may see in Event Viewer:
• The provided anti-forgery token was meant for a different claims-based user than the current user.
• The provided anti-forgery token was meant for user “”, but the current user is “X”.
• The anti-forgery cookie token and form field token do not match.
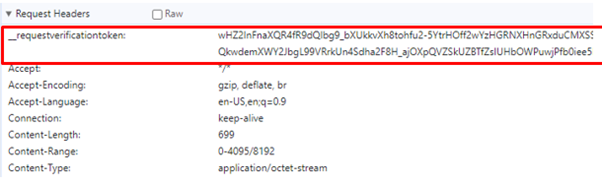
• The required anti-forgery cookie “__RequestVerificationToken” is not present.
We encountered this anti-forgery cookie error while pushing the file from Portal to File type column in one of the records. I have an entity called Common Attachments and have added PCF control to save the file as file attachment using new column type called “File”. Please refer to the below link for more details about this new field type.
https://learn.microsoft.com/en-us/power-apps/developer/data-platform/file-attributes?tabs=sdk
The following screenshot shows an interface which is implemented in the portal.
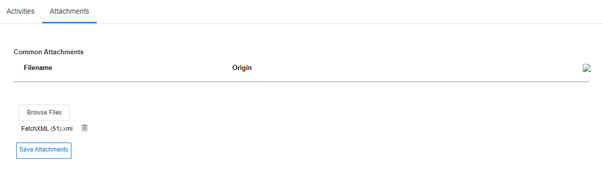
In this article, we are going to share the error which I encountered related to authorization and the resolution of the same.
Troubleshooting
401 Unauthorized Error is an HTTP reaction rating code illustrating that an application made by the client has not been verified.
While debugging the Jscript, we can see the following details where status of the REST call shows 401 Unauthorized.
“Request validation failed: The required anti-forgery form field “__RequestVerificationToken” is not present.” while executing REST call in D365 portal.
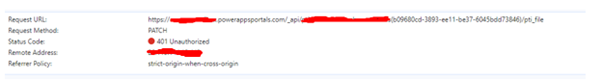
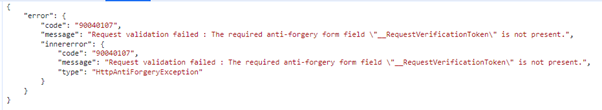
What is RequestVerificationToken?
The __RequestVerificationToken is a hidden form field that is injected at the end of every form. It contains an encrypted value that represents the token. The value is also sent to the browser in the same site cookie.
Request verification tokens, also known as anti-forgery tokens, are used to prevent CSRF in ASP.NET. These tokens are randomly generated values that are included in any form or request that needs protection.ASP.NET MVC uses anti-forgery tokens to prevent CSRF attacks. When a client requests an HTML page that contains a form, the server includes two tokens in the response. One token is sent as a cookie.
Solution
As mentioned above __RequestVerificationToken is already stored in a hidden field on the form just retrieve its value and send as header to REST call.
Usage
Use the following lines of code to authorize the request.
var inputRequestToken = document.getElementsByName("__RequestVerificationToken")[0].defaultValue;
var req = new XMLHttpRequest();
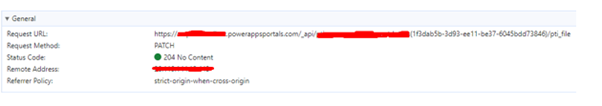
req.open("PATCH", url, false);
req.setRequestHeader("__requestverificationtoken", inputRequestToken);
After implementing the above code
After authorizing the REST call, it validates using the token as follows.
Summary
Cookie-based authentication is a popular form of authentication.
The ValidateAntiForgeryToken attribute requires a token for requests to the action methods it marks, including HTTP GET requests. If the ValidateAntiForgeryToken attribute is applied across the app’s controllers, it can be overridden with the IgnoreAntiforgeryToken attribute.
You can protect HTTP GET requests sent as a result of resource inclusions and links can by appending a relevant token in the “href” or “src” attributes. Include these tokens manually using provided JSP tag library or by using a JavaScript based automated injection mechanism. AJAX requests are protected by injecting an additional header, which contains a CSRF token.


